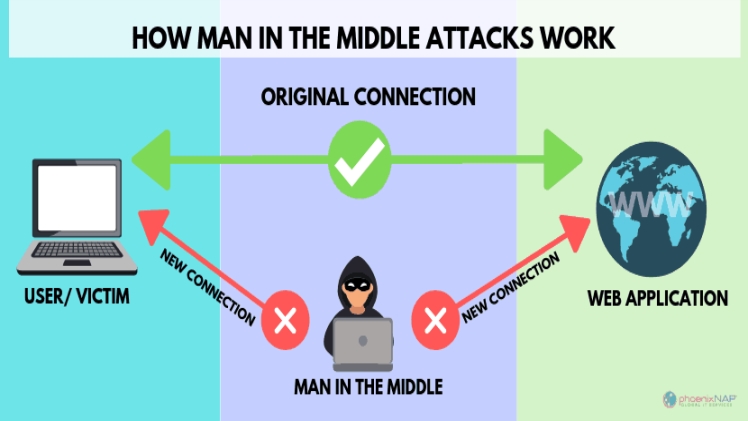
Man-in-the-middle (MiTm) assaults are a type of cyber-attack:
A man-in-the-middle (MiTM) attack occurs when an attacker places himself between two users in order to listen in on their conversation or disrupt data transmission. A MiTM attack is a sort of cyberattack in which an attacker acts as a quiet observer and manipulator, intercepting communication and message exchanges between two parties.
MiTM Attacks and Their Types
Victims are targeted via a variety of MiTM assaults. Here are a few of them:
Email Hijacking:
An attacker uses the victim’s email account to get access to communications between the victim and a target institution (such as a bank). The attacker pays special attention to transactions that take place between the two parties. From here, the attacker can communicate precise instructions by impersonating one or both participants. For example, an attacker may impersonate a bank’s email address and request sensitive information in order to gain access to the victim’s account or conduct fraudulent activities.
Hijacking a Session:
This can happen as a result of a cross-site scripting (XSS) attack or the theft of session browser cookies. When a user connects to their bank account, for example, an attacker may be watching and stealing the session cookie while the user is still logged in. The assailant can now move all of the funds from that account to his own.
Eavesdropping on Wi-Fi:
An attacker creates legitimate-sounding Wi-Fi connection names or public Wi-Fi connections that do not require a password in this scenario. Users are persuaded to join the network in the mistaken belief that they would be able to surf the network at no additional cost or effort. For example, if a user sees a Wi-Fi network titled ‘New York Airport,’ they may believe it is a real Wi-Fi connection offered by the New York Airport authority. The attacker will be able to access the victim’s activity after they join the infected network.
Read More About: newszone787
Spoofing an IP Address:
An attacker modifies the headers of packets in an IP address. For instance, if a user tries to access a legal e-commerce site and the IP address header is tampered with, the user will be routed to a phoney site that looks identical. The monies are moved to other accounts when a transaction is begun.
Visit the site: wapking
Spoofing DNS:
This procedure, also known as DNS cache poisoning, involves a hacker infiltrating a DNS server and modifying the website address record to match their own. If a user tries to access a real website and DNS spoofing happens, the user will be routed to the bogus URL through the changed DNS record. Any sensitive information sent by the victim will now be redirected to the attacker.
Spoofing HTTPS:
In this case, domains that seem identical to the original HTTPS domain with slight differences in non-ASCII characters are utilized to trick users into thinking they are communicating with trustworthy websites.
MiTM Attacks and How to Prevent Them
You may use the following recommended practices to prevent MiTM attacks if you’re a corporation wanting to safeguard your application data:
WAP Encryption on Access Points should be implemented:
Attackers can’t get into systems because of strong wireless application protocol (WAP) encryption.
VPN use:
Using a VPN to monitor traffic between endpoints and the server can help prevent MiTM attacks. Because it employs key-based encryption, it will be impenetrable to attackers from neighbouring shared networks.
Only make HTTPS connections:
Hackers will be unable to steal information as a result of this. There are additional browser plugins that may be used to enforce this requirement and guarantee that HTTP equivalents are never utilized.
End-to-end encryption should be used for all types of communication:
Make sure you include a variety of communication channels, such as email, chat, website, video, and so on.
Employees Should Be Trained:
Empower your employees to see warning signals and notify appropriate teams in the event of an emergency, so it’s never too late to intervene.
Strong Authentication Protocols Should Be Invested In:
Through asymmetric cryptographic methods with public and private keys, public key-based authentication, or RSA, can assist improve passwords. When a user attempts to log into a system, the server will prompt them to submit a public key (stored in the location where they desire access) for authentication. Following that is a private key (which is kept safe on the user’s PC).
Get the Fundamentals Right:
Maintain security patches, utilize a password manager if possible, conduct frequent monitoring processes, and invest in multifactor authentication.
Appsealing provides solutions for all kinds of cyber attacks.
If You Need More Information Visit: getinstagram